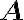Special | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z | ALL
I |
|---|
Idempotence | ||||||||
|---|---|---|---|---|---|---|---|---|
A square matrix, , is idempotent if it is equal to its square, i.e., [Ber18, Definition 4.1.1]. Notable properties: References
| ||||||||
Individual attack | ||||||||
|---|---|---|---|---|---|---|---|---|
The discussion here continues from the discussion of security of quantum key distribution (QKD). QKD is a method for generating and distributing symmetric cryptographic keys with information-theoretic security based on quantum information theory [ETS18]. In a QKD protocol,
😈 Eve’s attempt to discover the secret key can be classified into 1️⃣ individual attack (discussed below), 2️⃣ collective attack, and 3️⃣ coherent attack; in 🔼 increasing order of power given to Eve. Individual attacks are the simplest and most studied class of attacks. When conducting an individual attack, Eve interacts with each signal (i.e., quantum state) from Alice individually, and is restricted to the same interaction for all Alice’s signals [Sch10, Wol21].
Regardless, Eve has the freedom to choose which unitary operation she applies to a composite system (“composite” because more than one qubit is involved). Of interest is the amount of information about a single state that Eve gains with an attack. A standard measure of amount of information is mutual information. Perhaps the most intuitive example of an individual attack is the intercept and resend (I&R) attack [Sch10, Sec. 5.2.1]. References
| ||||||||