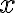Special | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z | ALL
A |
|---|
Abstract interpretation | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
High-level overviewAbstract interpretation, first formalised by Cousot and Cousot in 1977 [CC77], executes a program on an abstract machine to determine the properties of interest [vJ11, p. 1255]. The level of detail in the abstract machine specification typically determines the accuracy of the results. At one end of the spectrum is an abstract machine that faithfully represents the concrete semantics of the language. Abstract interpretation on such a machine 👆 would correspond to a concrete execution on the real machine. Typical abstract interpretation analyses, however, do not require detailed semantics. A bit of theoryFundamentally, the correctness problem of a program is undecidable, so approximation is necessary [Cou01, Abstract]. The purpose of abstract interpretation is to formalise this idea 👆 of approximation; see Fig. 1. Formally, abstract interpretation is founded in the theory for approximating sets and set operations [Cou01, Sec. 2]. The semantics of a program can be defined as the solution to a fixpoint (short for fixed point) equation. Thus, an essential role of abstract interpretation is providing constructive and effective methods for fixpoint approximation and checking by abstraction. By observing computations at different levels of abstraction (trace semantics → relational semantics → denotational semantics → weakest precondition semantics → Hoare logics), fixpoints can be approximated. Fig. 1: In abstract interpretation, the program analyzer computes an approximate semantics of the program [Cou01, Fig. 12]. The generator generates equations/constraints, the solution to which is a computer representation of the program semantics.The solver solves these equations/constraints. The diagnoser checks the solutions with respect to the specification and outputs “yes”, “no” or “unknown”. References
| ||||||||||
Address space layout randomisation (ASLR) | ||||
|---|---|---|---|---|
Address space layout randomisation (ASLR) refers to the randomisation of the locations of the key components of an executable — stack, heap, libraries and memory-mapped files, executable code — in the address space; to mitigate remote code execution and other attacks targeting CWE-787 and CWE-125. Watch Dr. Yeongjin Jang’s lecture on ASLR: ASLR targets memory corruption vulnerabilities such as buffer overflows, which typically occur when data get written to memory that is smaller than the size of the data — a common programming error when using a memory-unsafe language like C. By introducing uncertainty into the locations of the shellcode (or any other attack code), ASLR hinders exploitations of memory corruption vulnerabilities. There are many ways ASLR can be done, and different operating systems do it differently. There are three dimensions to be considered [MGRR19]: When This is about when the entropy used for ASLR is generated (see Table 1):
What This is about what to randomise. In the extreme, if a single object (e.g., the executable) is not randomised, ASLR is considered to be broken. An “aggressive” form of ASLR is when the randomisation is applied to the logical elements contained in the memory objects: processor instructions, blocks of code, functions, and even the data structures of the application; see Table 1. In this case 👆, the compiler, linker and loader are required to play an active role. This form of ASLR is not known to be in use. How Table 1 lists the main strategies:
References
| ||||
Advanced persistent threat (APT) | ||||
|---|---|---|---|---|
Advanced persistent threat (APT, see Definition 1) has been occupying the attention of many cybersecurity firms. Definition 1: Advanced persistent threat (APT) [NIS11, Appendix B]
An adversary that possesses sophisticated levels of expertise and significant resources which allow it to create opportunities to achieve its objectives using multiple attack vectors (e.g., cyber, physical, and deception). These objectives typically include establishing and extending footholds within the information technology infrastructure of the targeted organisations for purposes of exfiltrating information, undermining or impeding critical aspects of a mission, program, or organization; or positioning itself to carry out these objectives in the future. The advanced persistent threat: 1️⃣ pursues its objectives repeatedly over an extended period of time; 2️⃣ adapts to defenders’ efforts to resist it; and 3️⃣ is determined to maintain the level of interaction needed to execute its objectives. Since APT groups are characterised by sophistication, persistence and resourcefulness, they are challenging to counter. Lists of APT groups are being actively maintained, e.g., by MITRE and Mandiant. References
| ||||
Application security testing | ||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Application security testing can be static or dynamic. Static application security testing (SAST) is a specialisation of static (code/program) analysis. Watch an introduction to static code analysis on LinkedIn Learning: Static analysis from Developing Secure Software by Jungwoo Ryoo Exploring tools for static analysis from Developing Secure Software by Jungwoo Ryoo Definitions and history:
Challenges:
Tools:
Dynamic application security testing (DAST) is a specialisation of dynamic (code/program) analysis. Watch an introduction to dynamic code analysis on LinkedIn Learning: Dynamic analysis from Developing Secure Software by Jungwoo Ryoo Dynamic analysis tools from Developing Secure Software by Jungwoo Ryoo Definitions and history:
Challenges:
Tools: References
| ||||||||||||||||||||||||||||
Asymmetric-key cryptography | ||
|---|---|---|
Authenticated encryption with associated data (AEAD) | |||
|---|---|---|---|
See 👇 attachment (coming soon) or the latest source on Overleaf. | |||