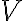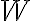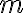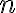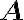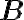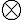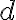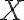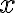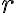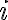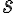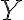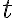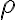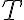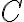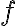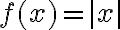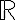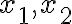Special | A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z | ALL
C |
|---|
Composite quantum systems | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
Consider a multi-qubit system consisting of two qubits. There are four possible final states: ; and it makes sense to express the quantum state of this two-qubit system as the linear combination: where the normalisation rule still applies: An alternative representation of is where the subscript indicates the order of the system. Some authors call the set , and equivalently , the tensor base [Des09, p. 316]. Watch Microsoft Research’s presentation on “Quantum Computing for Computer Scientists”: In the vector representation, given two separated qubits: their collective state can be expressed using the Kronecker product (also called the matrix direct product and tensor product): Multiple shorthands exist for : 1️⃣ , 2️⃣ , 3️⃣ [Mer07, p. 6; NC10, Sec. 2.1.7]; we have used the third shorthand earlier. In general, we can compose the Hilbert space of a multi-qubit system using the vector space direct product (also called tensor direct product) of lower-dimensional Hilbert spaces [NC10, Sec. 2.1.7]:
Classical-quantum stateIn quantum cryptography, we often encounter states that are partially classical and partially quantum. A classical state (c-state for short) is a state defined by a density matrix that is diagonal in the standard basis of the -dimensional state space of , i.e., has the form: Suppose we prepare the following states for Alice and Bob: with probability 1/2, we prepare and with probability 1/2, we prepare . Then, the joint state is the so-called classical-quantum state (cq-state for short): In quantum-cryptographic convention,
Formally,
References
| ||||||||||||
E |
|---|
Entropy | ||||||||
|---|---|---|---|---|---|---|---|---|
The following introduces Shannon entropy before von Neumann entropy. Shannon entropyThe Shannon entropy of a random variable, say , measures the uncertainty of . Intuition:
The following definition of entropy, denoted by , measured in number of bits, can reflect the two extreme cases above [MC12, Definition 5.4]: where denotes the probability of taking on the th value. Note: 1️⃣ ; 2️⃣ number of bits is discrete in practice but as a metric of comparison, we need entropy to be a continuous-valued metric. If has possible values, and has , the joint entropy of and is defined as [MC12, Definition 6.2]: The conditional entropy of given is defined as [MC12, (6.53)]: The chain rule for entropy states [MC12, p. 151; Gra21, (2.48)]: or more generally, Von Neumann entropyThe Shannon entropy measures the uncertainty associated with a classical probability distribution. Quantum states are described in a similar fashion, with density operators replacing probability distributions. The von Neumann entropy of a quantum state, , is defined as [NC10, Sec. 11.3]: where denotes the base-2 logarithm of and not the element-wise application of base-2 logarithm to . Watch an introduction to the matrix logarithm on YouTube: References
| ||||||||
F |
|---|
Fidelity | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
This entry continues from discussion of trace distance. [Des09, (22.8)]. [Hay17, Sec. 3.1.2 and Sec. 8.2]. [Le 06, (7.20)]. [Dio11, (6.19)]. [NC10, (9.2)]. [BS98, Sec. II]. References
| ||||||||||||||
G |
|---|
Galois field / finite field | |||
|---|---|---|---|
See abstract algebra.
| |||
Group theory | |||
|---|---|---|---|
See abstract algebra.
| |||
I |
|---|
Idempotence | ||||||||
|---|---|---|---|---|---|---|---|---|
A square matrix, , is idempotent if it is equal to its square, i.e., [Ber18, Definition 4.1.1]. Notable properties: References
| ||||||||
Individual attack | ||||||||
|---|---|---|---|---|---|---|---|---|
The discussion here continues from the discussion of security of quantum key distribution (QKD). QKD is a method for generating and distributing symmetric cryptographic keys with information-theoretic security based on quantum information theory [ETS18]. In a QKD protocol,
😈 Eve’s attempt to discover the secret key can be classified into 1️⃣ individual attack (discussed below), 2️⃣ collective attack, and 3️⃣ coherent attack; in 🔼 increasing order of power given to Eve. Individual attacks are the simplest and most studied class of attacks. When conducting an individual attack, Eve interacts with each signal (i.e., quantum state) from Alice individually, and is restricted to the same interaction for all Alice’s signals [Sch10, Wol21].
Regardless, Eve has the freedom to choose which unitary operation she applies to a composite system (“composite” because more than one qubit is involved). Of interest is the amount of information about a single state that Eve gains with an attack. A standard measure of amount of information is mutual information. Perhaps the most intuitive example of an individual attack is the intercept and resend (I&R) attack [Sch10, Sec. 5.2.1]. References
| ||||||||
K |
|---|
Kraus operator and Kraus representation | ||
|---|---|---|
L |
|---|
Linear operator | ||||
|---|---|---|---|---|
Let and be vector spaces. The mapping is called a linear transformation if and only if for every choice of and scalar . When , is called a linear operator [DG09, p. 202]. References
| ||||
Lipschitzness, Lipschitz condition | ||||||
|---|---|---|---|---|---|---|
Mathematical programming (theory-based optimisation methods as opposed to heuristics) works best with differentiable cost/loss functions. Mathematical programming also works with continuous loss functions [Byr15]. Differentiability implies continuity but the converse is not true, so continuity is a weaker condition than differentiability. For example, piecewise continuous functions are not differentiable at all points. Lipschitzness is a particular form of continuity. Strictly speaking, Lipschitzness is a form of uniform continuity: Definition 1: Lipschitzness [SSBD14, Definition 12.6]
It follows from the definition above that if the derivative of is everywhere bounded in absolute value by , then is -Lipschitz. References
| ||||||